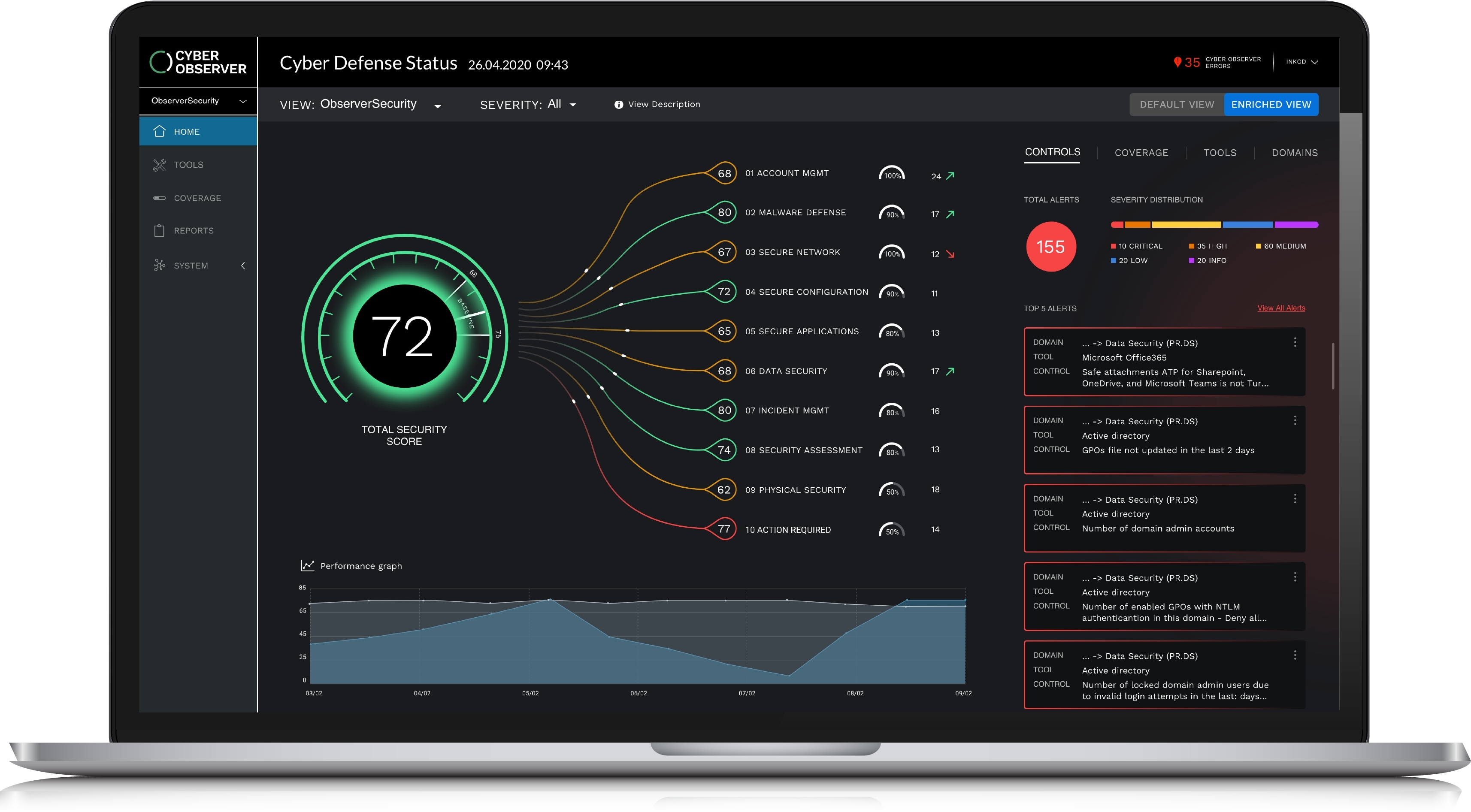
Cyber Observer's Latest Release Provides New Visibility Into Cybersecurity Risk Posture | Business Wire

Cybersecurity – Protecting people in their digital life with security at the foundation of everything we do - Telenor Group

39,800+ Security Monitoring Illustrations, Royalty-Free Vector Graphics & Clip Art - iStock | Cyber security monitoring, Home security monitoring, Security monitoring room






















